Lab 1 - Introduction to System Administration¶
Welcome to the System Administration course. Before getting started, please make sure you have read the following information:
- Courses Homepage for information about the Course Info
- Lecture slides for more detailed Course Information.
- Slack page for communication through Slack.
For any questions, we recommend using the Slack channels, as this will also make answers visible to other people.
Labs¶
This course is set up mainly in lab sessions, all labs every week follow the same format - a weekly guide in the Practicals page that works you through setting up a system or a service, or some closely related systems and services. Often enough, a next week's lab might need settings to be changed in the previous lab's topic, for example, the web servers lab will require changes in things done in the domain name servers lab. That's just how IT works.
Info
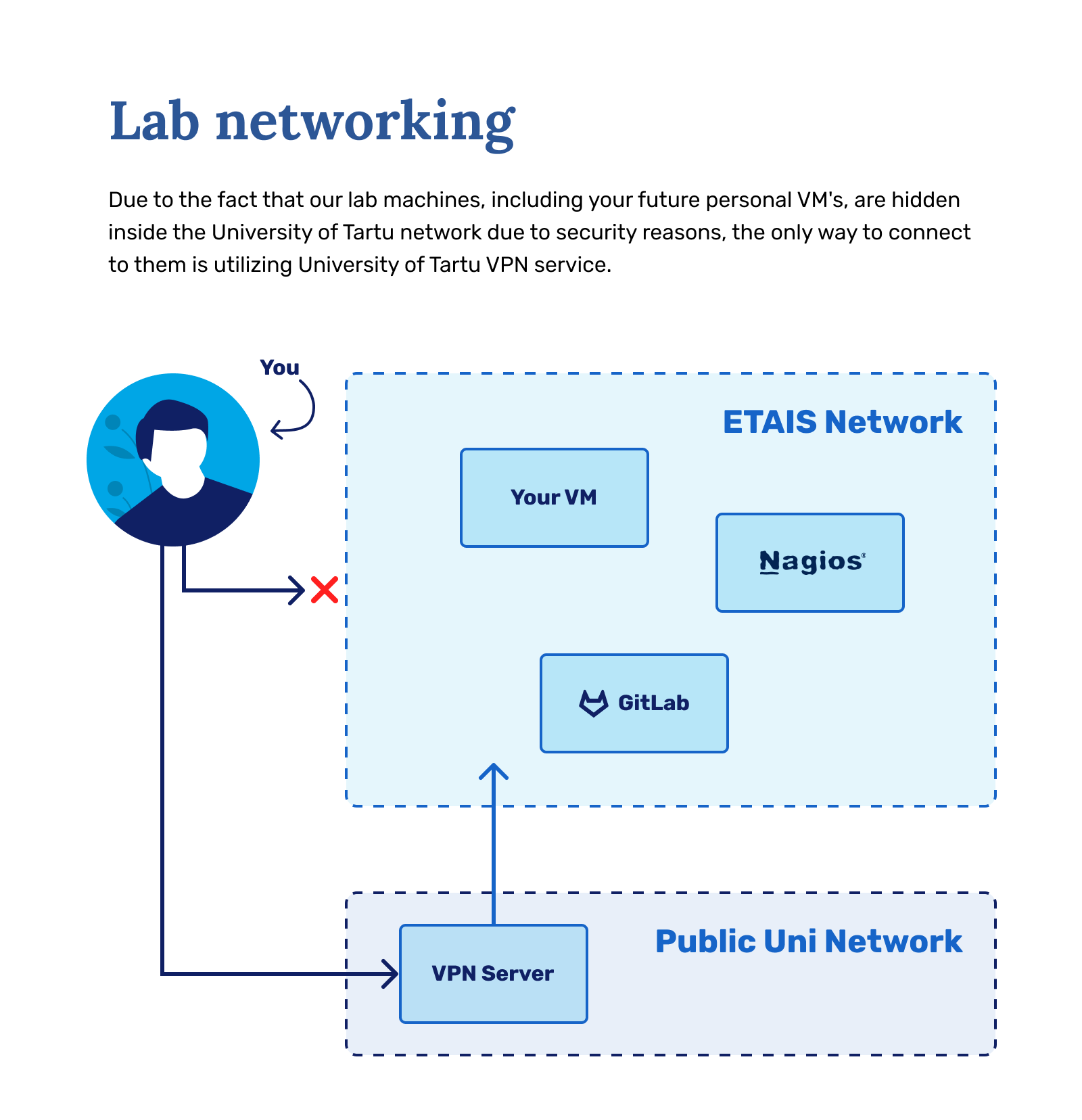
Lab1 environment and future personal VMs are only available inside the university network.
Scoring¶
During the course, you will be monitored and scored by a scoring server. This site monitors the progress of all the labs that you complete. When you are completing labs, you can see that you did everything right when monitoring goes green.
Once you access the scoring site, you can search for Services on the left side panel. When you click on it, a new view appears, where there's a host called "Lab1." From there, search a line with your username in it (it appears for the first time a bit after you log into lab1.sysadm.ee). When this line goes green, you have completed this week's task.
During the next weeks, when you get your own personal VM, you will have a line with your VMs name in the list. Every week, as we publish another lab with tasks, the monitored services list will also expand.
When monitoring your personal VMs, there are two types of checks - with one we log into your machine and check whether something looks as it should, and the other option is to query your machine from the outside world. This means that you can't expect things in Lab6 to work when Lab2 is not done, as, for example, we can't access your machine, because Lab2 is where you set our access up.
Remembering *NIX¶
During this week we will play through the exercises refreshing your UNIX knowledge. Starting from the next week we start building the real server-side service infrastructure. Therefore we find it critical for you to feel fluent with the command-line interface (CLI) of Linux. The outline of this lab is as follows:
Important
This week monitoring tests whether a task is done in the CTF part of the lab.
Helpful materials¶
Before we get started with the practical part of the lab, let's go over where to find information, as that is a large part of this whole course. Every lab will have new commands, systems, configuration files, log file locations, and weird error outputs, which is why we strongly recommend utilizing google to its full extent and to talk with each other. At first, writing up commands that you won't remember is a very good idea. We will never prevent you from being able to look at your notes, even during the exam. This means that if you want, you can make a cheat sheet, or just write up any commands that you think you will not be able to remember.
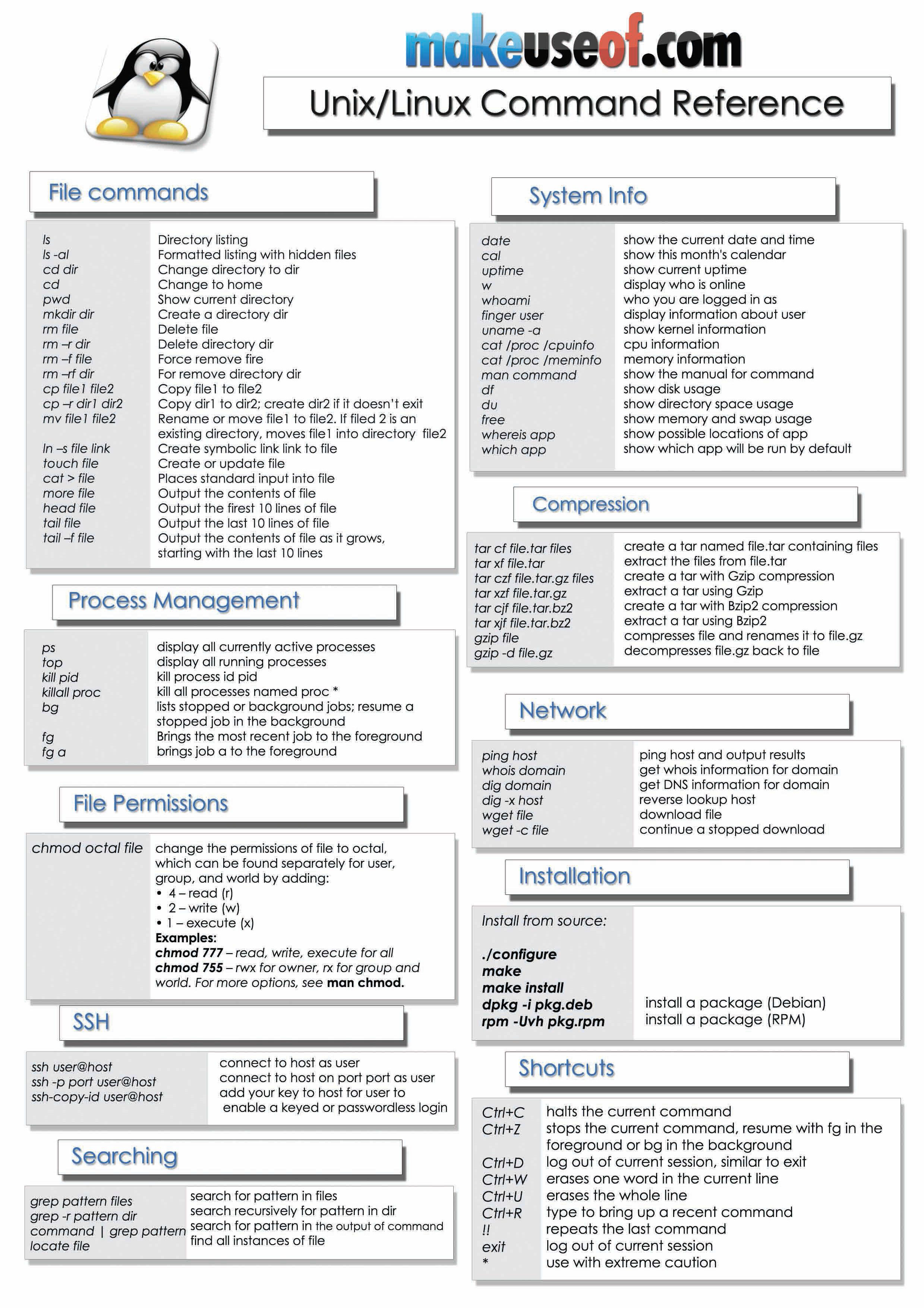
Automation is also not only allowed, but encouraged during the labs and the exam - in the following weeks we will also be teaching how to use a tool called Ansible, which will take care of config management and more. The third lab will be about Ansible best practices, and after that we add extra examples and guides about Ansible into the weekly labs as well. A well-written Ansible playbook could in theory allow you to pass the exam in just a few minutes, so keeping it up to date might prove invaluable. We will also try to provide you with informational visualizations to further your understanding. We hope these to be useful.
There are also remotely hosted resources that are very useful:
Especially Shell Commands Explainer, which takes the input command line, and tries to fully explain what is going on. Works for surprisingly many commands.
CTF¶
We now get to the practical part of the lab. Before we can do anything, we need to get inside the environment where we can play around without having to worry about our machines.
Accessing the Sandbox machine¶
First, make sure that you are connected to the University of Tartu network.
Remotely (not in the lab), this is achieved by using the University of Tartu VPN service. The guide for that can be found at UT wiki.
When you are using the classroom computers or University WIFI, you should be fine without the VPN.
Moving from one host to another on Linux systems is usually done by utilizing a protocol called SSH (Secure Shell). This can be used to login into another machine.
The syntax usually follows like this: ssh <username>@<hostname>
Example: ssh mouse@lab1.sysadm.ee
Complete
Let's log into a machine called lab1.sysadm.ee with our University of Tartu username and password.
The way to do this depends on which operating system you use currently:
For Linux/Mac (the classroom machines) users this can be done by opening your terminal application, and inserting the following command to the command line ssh <username>@lab1.sysadm.ee. You will be asked whether you trust the host and for your University of Tartu password.
You can tell whether you were successful logging in when you are not getting an error and if the shell prompt changes. Also, the output of commands whoami, hostname and pwd should be different from your own machine.
- Windows Subsystem for Linux - WSL(more info). Using WSL grants you the ability to open a Linux terminal in Windows, to use the ssh command as mentioned above. WSL is harder to set up, but easier and more convenient to use in the future, as it emulates the whole command line.
- If you get an error while installing Ubuntu, like:
error 0x80004002(or something similar with same code), please try the following fix in GitHub.
- If you get an error while installing Ubuntu, like:
- Software called PuTTY, that allows the creation of an SSH connection to the server. Putty is very easy to run, but in the future might cause you to need to jump through extra hoops to do some stuff, like add an SSH key. A guide on using PuTTY can be found on the University HPC page.
CTF Exercise¶
Capture The Flag (CTF) is a form of exercise where the task is to find very specific "flags", hidden in the system or software by competitors or organizers. This is very prevalent in especially Cyber Security, and if you like the following game, make sure to check out this one.
In our case, we have prepared a small CTF as a way to test your Linux knowledge. Do not worry if you cannot do every task outright, some of these are deceptively difficult.
If you cannot think of a solution, do not know how to do something, or want an explanation, make sure to ask a teacher either directly or by using Slack.
The exercise here is to complete the CTF inside the lab1.sysadm.ee machine. Go task by task, and only continue when you have the "flag" from a previous task. Collect and write the flags down, as all first 12 make up a clue for task 13. Tasks 14-16 are independent.
In some cases, the input to the next task is the flag from the previous task.
The format of each flag is the following: SysAdm-{<flag>}
Examples:
-
String:
SysAdm-{flag}, flag:flag -
String:
SysAdm-{fish}, flag:fish
The flag is always inside curly brackets {}.
Task 1 - A file with Flag inside a local directory
When first logged into a server, you are automatically placed inside a folder. Wonder what's in here?
Helpful commands: ssh, ls, cat
What you revised:
- How to view directory contents
- How to read file contents
Task 2 - A Flag in a Hidden File
Some files in Linux are hidden and only visible when you specifically look for them. Try to find a hidden file in your home directory which contains the next flag.
Helpful Commands: ls -a, cat
What you revised:
- Hidden files in Linux start with a dot (.)
- How to view hidden files
Task 3 - A Flag as an output of a command from history
Gasp! Someone's been here and has done something .. nefarious? Need to follow the instructions from the file! Wonder if the command does something nefarious.. The string looks like gibberish but ends with '=' - this is a common sign of base64 encoding, which is often used to encode data into text.
Helpful commands: history, grep
What you revised:
- Command history is stored in history
- How to decode base64 encoded text
- Using pipes to combine commands
Task 4 - A Flag in an environment variable
Someone left a message in an environment variable, I wonder how hard it is to read backwards. Can you put it back together? It'd be a great idea to write it down for later, wouldn't it?
Helpful commands: env, grep, rev
What you revised:
- What environment variables are
- How to view and manipulate environment variables
- Text manipulation in Linux
Task 5 - extract a Flag from a compressed file
Within the server you've already connected to, a compressed file lies in wait, possibly harboring yet another piece of the puzzle. Who knows what secrets or flags it might contain?
Helpful commands: tar, ls, cat, grep
What you revised:
- Working with compressed files
- Common archive formats in Linux
- File extraction and viewing
Task 6 - A Flag in a broken symbolic link
In the digital shadows of the server, a symbolic link lies fractured, its path leading nowhere. This broken link conceals a secret, a flag that must be found and claimed.
Helpful commands: ls -l, ln -s, readlink, <tab>
Hint: Try to follow the path of the broken link from the start, may be it leads to an interesting file. For example, if the broken link points to /path/to/missing/file, the real file might be in /path/to/actual/file.
What you revised:
- Understanding symbolic links
- How to identify broken paths
- File system path structures
<tab>Use tab completion to explore directories
Task 7 - A file in the subdirectory, with a Flag in it's name
Apparently not. Wonder if there's anything else cool in any of the folders inside my home directory? There are an awful lot of them in subdirectory. Maybe I could find a file there?
Helpful commands: find, cd, ls, cat
What you revised:
- Recursive directory searching
Task 8 - A Flag in ssh
Within the SSH files lies a clue waiting to be discovered. Dive into the authorized keys to see if you can find anything out of the ordinary. Pay special attention to the usernames and scribble it somewhere.
Helpful commands: cat
What you revised:
- Location of SSH files ~/.ssh/
Task 9 - A Flag in a log file
Nothing of note in an empty file. Maybe in any of the log files? My user seems to only have permissions to /var/log/audit.log.. It's so long though...
Helpful commands: find, grep, vim, cat
What you revised:
- Log file locations
- Efficient log searching
Task 10 - A Flag inside a system file
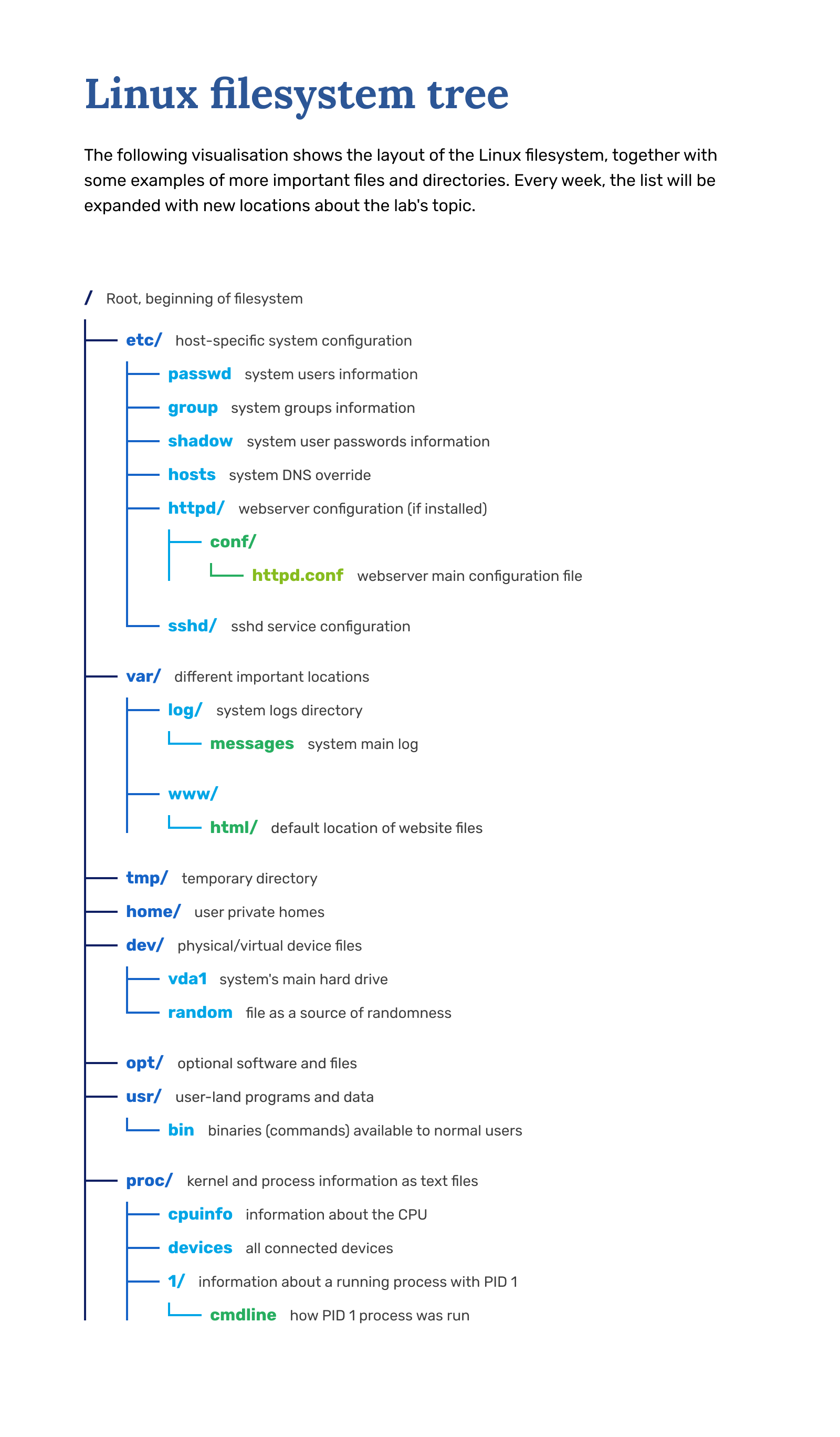
Maybe there's a user related to this whole ordeal? I'll check the Linux system user file under /etc/
Helpful commands: find, grep
What you revised:
- Location of user account info
Task 11 - A Flag received by executing a binary
That user has a weird command as their entrypoint /home/SysAdm/ctf.. Maybe my home directory has a similar file? Wonder what it does when I execute it..

Helpful commands: bash, ./, vim, cat, less
Hint: Make a new file
What you revised:
- How to execute local binaries
./ - Importance of reading
--help
Task 12 - A Flag in a running process
nobody is running a secret process that holds our flag. Can you find and extract what script holds?
Helpful commands: ps, grep, top, htop
What you revised:
- How to look up running processes
Task 13 - retrieve a Flag from a remote server
Using the credentials assembled from previous flags, discover what is waiting for you on the remote server. Maybe some treasure is there?
Helpful commands: rsync -av, scp, ssh
Hint: For credentials combine the flags of tasks 4, 8 and 12
Hint: Maybe try to ssh into the target to learn about the working directory and the file present.
What you revised:
- Remote file transfer
- Not to click on random links
Task 14 - A Flag in the output of a curl command
If you entered the previous machine, now is the time to return to Lab1 machine. This server (lab1) has a webserver running on port 80, let's try using curl on it.
Helpful commands: curl, netstat
What you revised:
- Web server interaction with
curl - Checking process running on parts with
netstat
Task 15 - A Flag in the output of nmap command
It gave us a port number... can we check ìf there is anything on that port? There's a tool called nmap for this!
Helpful commands: nmap -sV <hostname> -p <port>
What you revised:
- Port scanning
- Service detection
Task 16 - Flag can be received by sending a message to a port on localhost in the range 31000 to 32000
Port seems active, let's try sending data to this port. Using nc (netcat) and our university username.
Helpful commands: nc
NB!
The last task is monitored by the scoring server. It checks whether a correct username has been input as data into the port. It might take up to 5 minutes for monitoring to pick this up.
Endex?
endex in CTFs usually means "end of exercise".
Once the check in scoring is green, you're done with this week's lab. Congratulations!
Epilogue¶
By the end of the lab, make sure you have done all the following things, as a preparation to the next weeks:
- Have the capability of logging into a Linux host with SSH
- Are able to connect to the University of Tartu VPN (personal machines).
- Can access the Scoring website
- Have access to our course's Slack channels.
- Are knowledgeable about the topics and can find information related to the course.
- Have brushed up your google skills.
If missing anything, ask!